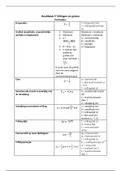
Checking that the result of any change to a signed integer
How is integer overflow/underflow mitigated?
falls within an allowed range.
In which file are password hashes stored on a modern
/ect/shadow
Linux system?
Load balancers are a service that distribute traflc evenly
across multiple containers or instances.
Which of the following is a network load balancer func-
A CDN distributes content based on location. A reverse
tion?
proxy forwards requests to backend hosts. A container
service such as ECS manages and scales containers to
meet demand.
Network Load Balancer Used to route TCP or UDP traflc.
Application Load Balancer Used to route HTTP or HTTPS
Disable the Banner
What can an Apache server administrator do to prevent
version information from leaking? Depending on the webserver, Apache or Nginx will out-
put their version number and some basic configuration
A) Run Apache as a non-root user information. For example, in Apache this is called the
B) Enable HTTPS 'signature'. This information can be valuable to attackers
C) Set permission on /var/www/html to 700 as it can leak what the specified version is running on
D) Disable the banner the server. This specified version may be vulnerable to a
specific exploit.
What can be inferred from the following Linux terminal
command? A normal account is attempting to view contents of a file
with root privileges
bobuser@ubuntu: ~$ sudo cat /ect/passwd
What is the process of preserving and evaluating electron-
Digital Forensics
ic data in order to reconstruct prior events?
Kernel
, The Kernel is responsible for loading programs, handling
Which computer component manages ongoing access to
input and output between peripherals, and managing
a computer's shared RAM and drive storage resources?
access to the computers shared hardware resources
Which of the following describes the files store under /etc
Configuration Data
folder in Linux?
JavaScript
Other languages used for website:
PHP
Which of the following programming languages is com- Python
monly used for website development? JAVA
Perl
ASP
Ruby
Go
What is found at the bottom of a stack frame when a
Return Pointer
function is called?
During which stage of incident response might a mass
password reset for every account on the network be per- Recovery
formed?
Which assembly register keeps track of the next instruc-
EIP
tion code to execute?
Directory Traversal
What type of attack is being attempted with the below
URL? The URL is attempting to naviagate to ../../../proc/mounts
http://www.the- which is a Directory Traversal attack. This takes advantage
of a flaw which allows an attacker to move outside the
force.org/view.php?page=%2e%2e%2f%2e%2e%2fproc/mounts
normal path.
Context Switching
2/8