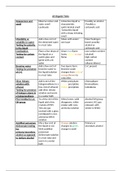
is and why you found it interesting. How does use of the MITRE frameworks
support understanding and discussion/collaboration on the report content you
have highlighted?
Answer & Explanation
The Cybersecurity and Infrastructure Security Agency (CISA) often utilizes the
MITRE ATT&CK framework to enhance understanding and collaboration in
cybersecurity efforts. One aspect of the CISA that I find particularly interesting
is its focus on threat intelligence sharing, which is crucial for preemptively
identifying and mitigating cyber threats.
Why It's Interesting: Threat intelligence sharing involves collecting,
analyzing, and disseminating information about potential or existing threats to
an organization's cybersecurity posture. This proactive approach allows
organizations to better prepare for attacks by understanding adversary tactics,