/ qn Don't launch with a graphical user interface.
Don't try to run as administrator, run as a normal user instead (this
/i
won't matter because of AlwaysInstallElevated).
/quiet Don't show the user any messages.
1 kilobyte = 1024 bytes. IEC introduced KiB instead: 1 byte is 8
bits. 1 kibibyte (KiB) is 1024 bytes. 1 mebibyte (MiB) is 1024
1024?!
kibibytes. 1 gibibyte (GiB) is 1024 mebibytes. 1 tebibyte (TiB) is
1024 gibibytes.
A system that allows the server to communicate with Windows
desktops, allowing the administrator to easily configure all the
connected desktops from one location, amongst other uses
Active Directory
which we will cover in future modules. Active Directory allows
administrators to configure settings on Windows desktops that
are connected to a Windows server.
Adding a new user is as simple as running: net user /add
<username> <password> This command will create a new user
Adding a new user and set the password to what you specified. You can do so much
more when creating users this way, such as configuring account
expiry and setting times where the account can log on.
Microsoft Word allows for third parties to write 'add-ins', which
Add-ins
extend the functionality of Microsoft Word.
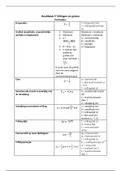
Volatility is one of the most widely used memory forensics tools.
Advanced Memory Forensics
Useful Volatility commands: imageinfo - vol.py or volatility -f
with Volatility
memdump.mem imageinfo
PowerShell comes with several aliases set up for common
Aliases
cmdlets. cat, cd, dir, ls, rm
We are very used to counting in base 10, but other number bases
Alternate Number Bases like base 16 (hex) or base 2 (binary) are incredibly useful in
computing.
, No two search engines are the same. Alternative Search Engines
Alternative Search Engines
- Google, Bing, Yahoo, DuckDuckGo, archive.org
Some administrators will configure this so that users can install
AlwaysInstall Elevated
software on their computers without administrator approval.
Analytics Collecting stats and analysing interactions on a web server.
Cyber criminals improve and modify their operational security
(OpSec) in order to avoid being caught. NotPetya is part of the
Anti Forensics
Petya family of encrypting ransomware that targets Microsoft
Windows based systems.
The Apple File System supports permissions and encryption, and
duplicate files can be stored without using additional space, with
APFS changes to one copy of a file being saved as a delta (the
difference between the old file and the new file) to lower space
requirements.
An example of an application layer protocol is something like
HTTP or FTP. HTTP GET request is an application layer protocol
Application Layer
because the web browser will form the request necessary for
displaying a page or submitting a form.
The 'apropos' tool is used to search man pages for keywords,
usually to find the 'appropriate' tool to use in a particular
apropos
situation. The 'apropos' command is used to find the 'appropriate'
tool for a particular job.
The apt command is incredibly useful to rapidly find, install, or
remove software. The way 'apt' works is by having a list of
apt-get 'sources'; these are servers which contain information about
available packages, download links and version information. 'apt
update' only updates the list of available packages.
The 'argc' variable is an integer which contains the number of
Arguments arguments passed to the program when it was executed. The
'argv' array contains the data passed in.
The Arithmetic Logic Unit is the part of the CPU responsible for
Arithmetic Logic Unit (ALU)
performing arithmetic and logical operations.
The Address Resolution Protocol translates IP addresses to MAC
ARP addresses for transmission purposes. ARP is only for the local
network.
ARP (address resolution protocol) is a protocol used on local
networks to map IP addresses to MAC addresses. When a
ARP Cache
computer receives an ARP response, it saves it into the ARP
cache.
The flaw in the ARP protocol comes because, if an ARP response
ARP Spoofing / Poisoning is sent to a computer, it will store that value in its ARP cache even
if it didn't make an ARP request asking for a response.
In C, you have to specify the type of the array when you create it,
Arrays and it can only ever hold that type of data. You can't mix and
match within the same array.
The AS keyword is used to assign an alias to a table or field.They
are used to make long SQL statements more readable, more
AS
descriptive or set the table headings for a query to make the
results more descriptive.