CERTIFIED ETHICAL HACKER
Latest uploads at CERTIFIED ETHICAL HACKER. Looking for notes at CERTIFIED ETHICAL HACKER? We have lots of notes, study guides and study notes available for your school.
-
80
- 0
-
12
All courses for CERTIFIED ETHICAL HACKER
-
CERTIFIED ETHICAL HACKER 77
Latest content CERTIFIED ETHICAL HACKER
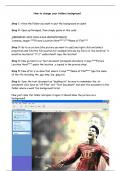
In this ebook you will learn change folder background.
- Package deal
- Summary
- • 1 pages's •
-
Certified Ethical Hacker•Certified Ethical Hacker
-
Learn hacking tips and tricks by Ebooks• Byadityakumar42
Preview 1 out of 1 pages
Getting your document ready...
In this ebook you will learn change folder background.

In these you will get know small-small tips and trick that will help you through ethical hacking journey.
- Package deal
- Summary
- • 3 pages's •
-
Certified Ethical Hacker•Certified Ethical Hacker
-
Learn hacking tips and tricks by Ebooks• Byadityakumar42
Preview 1 out of 3 pages
Getting your document ready...
In these you will get know small-small tips and trick that will help you through ethical hacking journey.

In-depth CEH study resource with over 40 pages of practice questions including answers and explanation to help you master the CEH Exam!
- Exam (elaborations)
- • 49 pages's •
-
Certified Ethical Hacker•Certified Ethical Hacker
Preview 4 out of 49 pages
Getting your document ready...
In-depth CEH study resource with over 40 pages of practice questions including answers and explanation to help you master the CEH Exam!

CERTIFIED ETHICAL HACKER Version 11 MASTER SET (Answered 2022/2023) Question Bank Which of the following information security elements guarantees that the sender of a message cannot later deny having sent the message and the recipient cannot deny having received the message? A Confidentiality B Non-repudiation C Availability D Integrity B A phase of the cyber kill chain methodology triggers the adversary's malicious code, which utilizes a vulnerability in the operating system, applic...
- Exam (elaborations)
- • 169 pages's •
-
CERTIFIED ETHICAL HACKER•CERTIFIED ETHICAL HACKER
Preview 4 out of 169 pages
Getting your document ready...
CERTIFIED ETHICAL HACKER Version 11 MASTER SET (Answered 2022/2023) Question Bank Which of the following information security elements guarantees that the sender of a message cannot later deny having sent the message and the recipient cannot deny having received the message? A Confidentiality B Non-repudiation C Availability D Integrity B A phase of the cyber kill chain methodology triggers the adversary's malicious code, which utilizes a vulnerability in the operating system, applic...

CERTIFIED ETHICAL HACKER Version 11 MASTER SET (Answered 2022/2023) Question Bank Which of the following information security elements guarantees that the sender of a message cannot later deny having sent the message and the recipient cannot deny having received the message? A Confidentiality B Non-repudiation C Availability D Integrity B A phase of the cyber kill chain methodology triggers the adversary's malicious code, which utilizes a vulnerability in the operating system, applic...
- Exam (elaborations)
- • 169 pages's •
-
CERTIFIED ETHICAL HACKER•CERTIFIED ETHICAL HACKER
Preview 4 out of 169 pages
Getting your document ready...
CERTIFIED ETHICAL HACKER Version 11 MASTER SET (Answered 2022/2023) Question Bank Which of the following information security elements guarantees that the sender of a message cannot later deny having sent the message and the recipient cannot deny having received the message? A Confidentiality B Non-repudiation C Availability D Integrity B A phase of the cyber kill chain methodology triggers the adversary's malicious code, which utilizes a vulnerability in the operating system, applic...

CLEAR CEH V12 EXAM IN YOUR FIRST ATTEMPT
- Exam (elaborations)
- • 880 pages's •
-
CERTIFIED ETHICAL HACKER•CERTIFIED ETHICAL HACKER
Preview 4 out of 880 pages
Getting your document ready...
CLEAR CEH V12 EXAM IN YOUR FIRST ATTEMPT

CERTIFIED ETHICAL HACKER Version 11 MASTER SET (Answered 2022/2023) Question Bank Which of the following information security elements guarantees that the sender of a message cannot later deny having sent the message and the recipient cannot deny having received the message? A Confidentiality B Non-repudiation C Availability D Integrity B A phase of the cyber kill chain methodology triggers the adversary's malicious code, which utilizes a vulnerability in the operating system, applic...
- Exam (elaborations)
- • 169 pages's •
-
CERTIFIED ETHICAL HACKER•CERTIFIED ETHICAL HACKER
Preview 4 out of 169 pages
Getting your document ready...
CERTIFIED ETHICAL HACKER Version 11 MASTER SET (Answered 2022/2023) Question Bank Which of the following information security elements guarantees that the sender of a message cannot later deny having sent the message and the recipient cannot deny having received the message? A Confidentiality B Non-repudiation C Availability D Integrity B A phase of the cyber kill chain methodology triggers the adversary's malicious code, which utilizes a vulnerability in the operating system, applic...

CERTIFIED ETHICAL HACKER Version 11 MASTER SET (Answered 2022/2023) Question Bank Which of the following information security elements guarantees that the sender of a message cannot later deny having sent the message and the recipient cannot deny having received the message? A Confidentiality B Non-repudiation C Availability D Integrity B A phase of the cyber kill chain methodology triggers the adversary's malicious code, which utilizes a vulnerability in the operating system, applic...
- Exam (elaborations)
- • 169 pages's •
-
CERTIFIED ETHICAL HACKER•CERTIFIED ETHICAL HACKER
Preview 4 out of 169 pages
Getting your document ready...
CERTIFIED ETHICAL HACKER Version 11 MASTER SET (Answered 2022/2023) Question Bank Which of the following information security elements guarantees that the sender of a message cannot later deny having sent the message and the recipient cannot deny having received the message? A Confidentiality B Non-repudiation C Availability D Integrity B A phase of the cyber kill chain methodology triggers the adversary's malicious code, which utilizes a vulnerability in the operating system, applic...

CERTIFIED ETHICAL HACKER Version 11 MASTER SET (Answered 2022/2023) Question Bank Which of the following information security elements guarantees that the sender of a message cannot later deny having sent the message and the recipient cannot deny having received the message? A Confidentiality B Non-repudiation C Availability D Integrity B A phase of the cyber kill chain methodology triggers the adversary's malicious code, which utilizes a vulnerability in the operating system, applic...
- Exam (elaborations)
- • 169 pages's •
-
CERTIFIED ETHICAL HACKER•CERTIFIED ETHICAL HACKER
Preview 4 out of 169 pages
Getting your document ready...
CERTIFIED ETHICAL HACKER Version 11 MASTER SET (Answered 2022/2023) Question Bank Which of the following information security elements guarantees that the sender of a message cannot later deny having sent the message and the recipient cannot deny having received the message? A Confidentiality B Non-repudiation C Availability D Integrity B A phase of the cyber kill chain methodology triggers the adversary's malicious code, which utilizes a vulnerability in the operating system, applic...
