AM Security
A. Describe the network topology that you found when running Nmap.
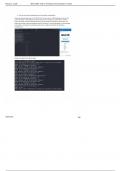
6 hosts were found using nmap -sn 10.168.27.0/24. The hosts are in a STAR topology as shown in the
screenshot below. A star topology means that all hosts are connected to a central device, usually a
switch. This makes it easier to add and take away new hosts with no disruption to the network. The
switch also provides a central management point for all devices. The major drawback to a star topology
is the switch or central device everything connects to is a single point of failure for all devices
connected to it.
A larger screenshot of the above image.
about:bla 1/6
nk
, 6/21/23, 11:08 WGU C844 Task 1 Emerging Technologies in Cyber
AM Security
B. Summarize the vulnerabilities on the network and their potential implications based on
NMAP results.
On 10.168.27.14, 10.168.27.20 and 10.168.27.132 I found that these devices are running on Linux kernel
2.6.32. This version has vulnerabilities such as CVE-2019-17351 which can be used to perform a denial
of service (DoSti attack. (Vulnerability Details: Cve-2019-17351ti
On 10.168.27.15 I found that FileZilla FTP is running on port 21. FTP is an insecure protocol that sends
data in clear text across the network making it an easy target for gaining usernames and passwords.
about:bla 2/6
nk