1. Introduction to Cybersecurity
Cybersecurity is the practice of safeguarding systems, networks, programs, and
data from digital attacks, damage, or unauthorized access. As the world becomes
more reliant on digital technologies, cybersecurity has grown in importance
across industries—from small businesses to large enterprises—and even to
individual users.
Cybersecurity aims to ensure the confidentiality, integrity, and availability of
information, often abbreviated as the CIA Triad, by defending against various
types of cyber threats. These threats can be malicious and pose risks to personal
data, business operations, and national security.
Why Cybersecurity Matters:
Protection from Cyberattacks: The frequency and sophistication of
cyberattacks have increased. Cybercriminals use various methods to gain
unauthorized access to systems for financial or personal gain.
Safeguarding Personal Data: Individuals' personal information, such as
addresses, payment details, and social security numbers, are highly
valuable to cybercriminals. Cybersecurity prevents identity theft and fraud.
Business Continuity: Companies face serious consequences if their data is
compromised. A major attack can halt operations, tarnish reputations, and
result in significant financial losses.
Legal and Regulatory Compliance: With global data protection laws such as
GDPR and HIPAA, organizations must comply with regulations to avoid fines
and reputational damage.
2. Types of Cybersecurity Threats
Understanding the types of cybersecurity threats is essential to implementing
effective protection strategies. Here are some of the most common threats in the
digital space:
, Common Cybersecurity Threats:
Malware: This umbrella term covers malicious software that disrupts
systems or steals sensitive data. Common types of malware include:
o Viruses: Programs that spread by attaching themselves to other files
and infecting systems.
o Ransomware: Software that locks files or systems and demands
payment for access to be restored.
o Trojans: Malicious software disguised as legitimate software to gain
unauthorized access to systems.
o Spyware: Programs that secretly collect user information without
consent.
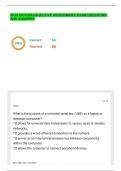
Phishing: Phishing attacks are fraudulent attempts by cybercriminals to
steal sensitive information by pretending to be legitimate entities, such as
banks, government agencies, or well-known companies. These attacks
typically happen via email, messages, or fake websites.
Man-in-the-Middle (MITM) Attacks: In a MITM attack, attackers intercept
communications between two parties (such as a user and a website) to
steal or alter the information being transmitted. This can happen on
unsecured Wi-Fi networks.
Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks:
These attacks overwhelm a target system, such as a website or server, with
an excessive amount of traffic, rendering it unavailable to legitimate users.
DDoS attacks often involve a botnet of compromised computers.
SQL Injection: SQL injection attacks occur when malicious SQL code is
injected into a vulnerable web application’s database query, allowing
attackers to execute commands, steal data, or manipulate the database.
Zero-Day Exploits: These attacks target vulnerabilities in software or
hardware that are unknown to the developer or vendor, meaning there is
no fix or patch available. Hackers exploit these "zero-day" vulnerabilities
before they are identified and fixed.
Social Engineering: Cybercriminals manipulate individuals into revealing
confidential information or performing actions that compromise security.
Common social engineering techniques include pretexting (creating a
fabricated scenario), baiting (enticing victims with promises), and tailgating
(gaining physical access to restricted areas).