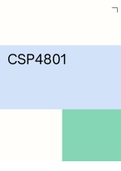
Pearson BTEC Level 3 Extended Certificate in Computing
Unit 7: IT Systems Security and Encryption
Learning Aim D:
D.P7 Perform tasks to protect the IT system to meet
requirements given in the plan.
D.P8 Explain the principles of information security
when protecting the IT systems of organisations.
D.M4 Review the extent to which the organisation’s IT
system has been protected.
,P7/M4 Implementing IT system security strategies
In this document I will be implementing strategies to enhance the protection of the IT system. This will be done by performing tasks which meet the
requirements given in the plan. The carrying out of security strategies is split into the following categories; group policies, anti-malware protection, firewall
configuration, wireless security and access control.
Group Policies
The use of a ‘Group policy’ is a good tool for managing both devices and IT systems. On Microsoft Windows it has a simple interface which allows
administrators to control user accounts, the working environment and device settings. One of the benefits of such system is that only the administrator has
the ability to change the policies, as he/she is one of only a few people to have full privileges -this increases security as normal users aren’t able to access
certain features and make changes.
Editing policies
STEP SCREENSHOT COMMENT
1
First, I pressed the ⊞ Win + R key to access the
run command and entered ‘gpedit.msc’.
This opened the ‘Local Group Policy Editor’.
2
Next, I clicked on ‘Administrative Templates’.
This allowed me to access a template of all the
features that could be controlled.
Unit 7: IT Systems Security and Encryption
,3
To protect the IT system and meet previously set
requirements, I will alter the following settings:
• Password Policy
• Remove Add or Remove Programs
• Prohibit access to Control Panel and PC
settings
• Prevent changing desktop background
• Prevent changing desktop icons
• Prevent addition of printers
• Allow shared folders to be published
• Prevent access to the command prompt
• CD and DVD: Deny write access
• Do not display ‘Install Updates and Shut
Down’ option in Shut Down Windows
dialog box
• Set rules for remote control of Remote
Desktop Services user sessions
4
To change the settings, I double clicked the setting
icon and this opened up a dialogue box.
I enabled each setting by changing the radio
button to ‘Enabled’.
Also, I left comments within some of the setting -
these would be used for any future reference.
To apply the settings to user accounts - before I
closed the window - I pressed ‘Apply’ in the
bottom right corner. This applied the changes to
every user on the domain.
Unit 7: IT Systems Security and Encryption
, 5 Finally, to ensure everything was applied, I tried to
access certain settings and features on a non-
admin account.
The ‘Restrictions’ error message came up when I
tried to access these features.
These changes enhanced the security on the IT system as the ensure that users don’t have access to areas such as the Control Panel and PC settings - areas
where changes could compromise the system - whilst not allowing CDs and DVDs to have write privileges as they could contain malicious software.
Additional changes include adding a password policy; this meets the requirements of every user having robust protection to their account. Having settings
on shared folders also meets prior set requirements that require only certain users to have access to certain folders or types of data.
Audit policy
STEP SCREENSHOT COMMENT
1 To access the auditing section within the policy editor,
I navigated to the ‘Audit Policy’ folder.
This is located at: Computer configuration ->
Windows Settings -> Security Settings -> Local
Policies -> Audit Policy
Within this folder there are nine different events
which can be setup to be audited.
Unit 7: IT Systems Security and Encryption
Unit 7: IT Systems Security and Encryption
Learning Aim D:
D.P7 Perform tasks to protect the IT system to meet
requirements given in the plan.
D.P8 Explain the principles of information security
when protecting the IT systems of organisations.
D.M4 Review the extent to which the organisation’s IT
system has been protected.
,P7/M4 Implementing IT system security strategies
In this document I will be implementing strategies to enhance the protection of the IT system. This will be done by performing tasks which meet the
requirements given in the plan. The carrying out of security strategies is split into the following categories; group policies, anti-malware protection, firewall
configuration, wireless security and access control.
Group Policies
The use of a ‘Group policy’ is a good tool for managing both devices and IT systems. On Microsoft Windows it has a simple interface which allows
administrators to control user accounts, the working environment and device settings. One of the benefits of such system is that only the administrator has
the ability to change the policies, as he/she is one of only a few people to have full privileges -this increases security as normal users aren’t able to access
certain features and make changes.
Editing policies
STEP SCREENSHOT COMMENT
1
First, I pressed the ⊞ Win + R key to access the
run command and entered ‘gpedit.msc’.
This opened the ‘Local Group Policy Editor’.
2
Next, I clicked on ‘Administrative Templates’.
This allowed me to access a template of all the
features that could be controlled.
Unit 7: IT Systems Security and Encryption
,3
To protect the IT system and meet previously set
requirements, I will alter the following settings:
• Password Policy
• Remove Add or Remove Programs
• Prohibit access to Control Panel and PC
settings
• Prevent changing desktop background
• Prevent changing desktop icons
• Prevent addition of printers
• Allow shared folders to be published
• Prevent access to the command prompt
• CD and DVD: Deny write access
• Do not display ‘Install Updates and Shut
Down’ option in Shut Down Windows
dialog box
• Set rules for remote control of Remote
Desktop Services user sessions
4
To change the settings, I double clicked the setting
icon and this opened up a dialogue box.
I enabled each setting by changing the radio
button to ‘Enabled’.
Also, I left comments within some of the setting -
these would be used for any future reference.
To apply the settings to user accounts - before I
closed the window - I pressed ‘Apply’ in the
bottom right corner. This applied the changes to
every user on the domain.
Unit 7: IT Systems Security and Encryption
, 5 Finally, to ensure everything was applied, I tried to
access certain settings and features on a non-
admin account.
The ‘Restrictions’ error message came up when I
tried to access these features.
These changes enhanced the security on the IT system as the ensure that users don’t have access to areas such as the Control Panel and PC settings - areas
where changes could compromise the system - whilst not allowing CDs and DVDs to have write privileges as they could contain malicious software.
Additional changes include adding a password policy; this meets the requirements of every user having robust protection to their account. Having settings
on shared folders also meets prior set requirements that require only certain users to have access to certain folders or types of data.
Audit policy
STEP SCREENSHOT COMMENT
1 To access the auditing section within the policy editor,
I navigated to the ‘Audit Policy’ folder.
This is located at: Computer configuration ->
Windows Settings -> Security Settings -> Local
Policies -> Audit Policy
Within this folder there are nine different events
which can be setup to be audited.
Unit 7: IT Systems Security and Encryption