Answered.
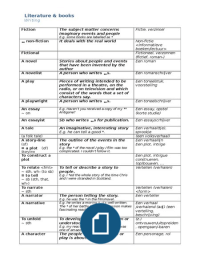
1. Directory
Trans- versal Finding a directory listing and gaining access to a parent or root file for
access to other files
2. Incremental
Sub- stitution Replacing numbers in a url to access other files
3. Vulnerabilit
y Scanning
The automated process of proactively identifying vulnerabilities of
4. Network computing systems present in a network
Scan- ning
A procedure for identifying active hosts on a network.
5. Port Scanning A series of messages sent by someone attempting to break into a
computer to learn about the computer's network services.
6. TCP SYN Scan -sS
7. TCP
connect() -sT
scan
8. FIN Scan -sF
9. Xmas Tree scan -sX
10. Ping Scan -sP
11. Version
Detec- tion -sV
Scan
12. UDP Scan -sU
13. IP Protocol Scan -sO
14. ACK Scan -sA
1/
3