Personal Folder of BTEC L3 IT Practitioners (Achived D*DD)
Former CANDI student studying Computer Forensics in Middlesex University. Achieved D*DD in BTEC L3 Extended Diploma in IT Practitioners. Work inspired by others and own research, only uploading theoretical documents.
I'd like to stress the fact that you should not completely copy the work, but use the provided work as a guide to what you need to write.
If you have any queries, feedback, or anything else. Feel free to send me a message and I'll reply as soon as possible!
- 75
- 0
- 1
Community
- Followers
- Following
65 Reviews received
76 items

P1 – Explain the key features of procedural programs
The first item you have been asked to supply is a reply to the frequently asked question (FAQ) ‘what is a procedural program?’ You need to describe the key features of procedural programs. To achieve this you must explain the features and control structures required to implement a given design. Describe the features and structures clearly and logically, outlining the reasons why the structures are important.
- Essay
- • 3 pages •
The first item you have been asked to supply is a reply to the frequently asked question (FAQ) ‘what is a procedural program?’ You need to describe the key features of procedural programs. To achieve this you must explain the features and control structures required to implement a given design. Describe the features and structures clearly and logically, outlining the reasons why the structures are important.

M2 – Give reasons for the tools and techniques used in the production of a procedural application
Justify your choice of tools and techniques used in the Airline Booking application. To achieve this you must explain how and why the methods declared are used, what parameters/data will be used and how data passes throughout the program. Evidence should be a short report, or similarly detailed presentation.
- Essay
- • 2 pages •
Justify your choice of tools and techniques used in the Airline Booking application. To achieve this you must explain how and why the methods declared are used, what parameters/data will be used and how data passes throughout the program. Evidence should be a short report, or similarly detailed presentation.

M3 - Judge the value of different sources of support material
Advice and Guidance Again using the DIONYSUS scenario, add a heading “Sources of Information” to show which books, internet sites, newsgroups, forums, manufacturer manuals etc… you referred to when trying to find how to resolve the reported fault. • You may include a variety of sources to meet the criteria. • Sources of information: You must include: • product specifications and manuals • colleagues with specialist expertise • manufacturers know...
- Essay
- • 2 pages •
Advice and Guidance Again using the DIONYSUS scenario, add a heading “Sources of Information” to show which books, internet sites, newsgroups, forums, manufacturer manuals etc… you referred to when trying to find how to resolve the reported fault. • You may include a variety of sources to meet the criteria. • Sources of information: You must include: • product specifications and manuals • colleagues with specialist expertise • manufacturers know...

M2 - Explain the advantages and disadvantages of outsourcing technical support
Explain the impact on the company and employees if their technical support was to be outsourced. • You work as an IT technician for DIONYSUS. What might be the effects for staff in DIONYSUS if IT were outsourced? Consider both the positive and negative effects. Write notes to explain the advantages and disadvantages of outsourcing technical support.
- Essay
- • 1 pages •
Explain the impact on the company and employees if their technical support was to be outsourced. • You work as an IT technician for DIONYSUS. What might be the effects for staff in DIONYSUS if IT were outsourced? Consider both the positive and negative effects. Write notes to explain the advantages and disadvantages of outsourcing technical support.

P3 - Identify the types of fault that can occur
• You should include a brief explanation as to why you think it is loss of service or poor performance for example. The fault may also be a virus related issue or it could be an error message which you will need to investigate on the internet what it means: • Fault: • type (choose at least one of the following) eg • loss of service • poor performance • virus • error messages
- Essay
- • 1 pages •
• You should include a brief explanation as to why you think it is loss of service or poor performance for example. The fault may also be a virus related issue or it could be an error message which you will need to investigate on the internet what it means: • Fault: • type (choose at least one of the following) eg • loss of service • poor performance • virus • error messages

P2 - Explain the impact of organisational policies and procedures on the provision of technical support
Report on the Working procedures and policies: • Organisational guidelines (choose at least one of the following) eg • reporting of faults . internet use . security • You must include: • service level agreements . confidentiality . sensitivity of information • Grading tips: Include the impact of organisational constraints as well as policies and procedures e.g. • Costs of resources required • Time • User expertise
- Essay
- • 2 pages •
Report on the Working procedures and policies: • Organisational guidelines (choose at least one of the following) eg • reporting of faults . internet use . security • You must include: • service level agreements . confidentiality . sensitivity of information • Grading tips: Include the impact of organisational constraints as well as policies and procedures e.g. • Costs of resources required • Time • User expertise

P1 M1 D1 Merged (Read description for more info)
P1 - Explain the tools and techniques used for technical support M1 - Discuss the importance of keeping fault logs D1 - Review a recent advance in support systems technology You work for the IT Support department of a publishing company. Your line manager has asked you to prepare a guide for new technical staff joining the company, which explains the tools and techniques used for technical support. You should prepare a PowerPoint slide show presentation. Tools - You must include: • software...
- Essay
- • 3 pages •
P1 - Explain the tools and techniques used for technical support M1 - Discuss the importance of keeping fault logs D1 - Review a recent advance in support systems technology You work for the IT Support department of a publishing company. Your line manager has asked you to prepare a guide for new technical staff joining the company, which explains the tools and techniques used for technical support. You should prepare a PowerPoint slide show presentation. Tools - You must include: • software...

M3 - Report on the business risks of insecure networks and how they can be minimised
To report on how the risks above are minimised, use the following headings which in fact correspond to a Network Administrator’s duties: Network Administrator duties • Keeping security software up to date • Firewalls are checked regularly • Privileges (who has what and why) are checked • No business decision should compromise the network and vice versa
- Essay
- • 4 pages •
To report on how the risks above are minimised, use the following headings which in fact correspond to a Network Administrator’s duties: Network Administrator duties • Keeping security software up to date • Firewalls are checked regularly • Privileges (who has what and why) are checked • No business decision should compromise the network and vice versa
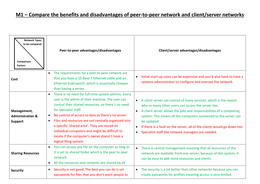
M1 - Compare the benefits and disadvantages of peer-to-peer network and client networks
One of CIT’s board members heard of peer-to-peer networks and believes that it would have been considerably less expensive to install and configure. Create a comparison table weighing the advantages against the disadvantages of peer-to-peer and client/server networks. In your Comparison table use the following comparison Headings: • Cost • Management/administration/support • Sharing Resources • Security • Size of network/ Scalability
- Judgments
- • 2 pages •
One of CIT’s board members heard of peer-to-peer networks and believes that it would have been considerably less expensive to install and configure. Create a comparison table weighing the advantages against the disadvantages of peer-to-peer and client/server networks. In your Comparison table use the following comparison Headings: • Cost • Management/administration/support • Sharing Resources • Security • Size of network/ Scalability

P5 - Describe typical services provided by networks
Directory services: a. active directory b. DNS c. account management d. authentication management 2. Telecommunication services: a. Email b. Internet relay chat (IRC) c. Discussion boards (newsgroups) d. Remote access e.g. via mobiles, remote desktop e. Social networking 3. File services: a. File transfer b. File sharing 4. Application services a. Application software e.g. database, web, proxy b. Shared resources e.g. printing; storage space c. Voice over IP (VoIP) d. Mobile working e. Authent...
- Essay
- • 5 pages •
Directory services: a. active directory b. DNS c. account management d. authentication management 2. Telecommunication services: a. Email b. Internet relay chat (IRC) c. Discussion boards (newsgroups) d. Remote access e.g. via mobiles, remote desktop e. Social networking 3. File services: a. File transfer b. File sharing 4. Application services a. Application software e.g. database, web, proxy b. Shared resources e.g. printing; storage space c. Voice over IP (VoIP) d. Mobile working e. Authent...

P2 & D1 - Explain and evaluate the impact of IT developments on an organisation
M1 - Compare the features and functions of different operating systems
Not what I needed
P4 - Explain how an organisation can manage risk when using IT technology
D1 - Discuss different ways of recovering from a disaster
D1 - Evaluate the impact of evolving output mediums on the design and creation of graphic images